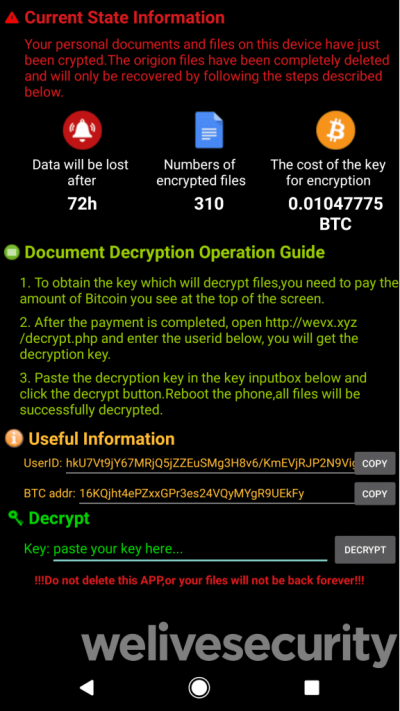
The ransomware — referred to as Android/Filecoder.C and active since July 12 — uses victims’ contact lists to spread further via SMS messages containing malicious links. The malware was distributed via pornographic posts on Reddit and XDA-Developers Android forum, the researchers noted. The SMS messages advertised a link to an app that has supposedly used the victim’s photos when it’s actually a malicious app containing the ransomware. In an attempt to hide their true motives, the attackers were sometimes found to mask the domain names using URL shorteners like bit.ly. The messages were also sent in one of 42 languages depending on the device’s language setting, and prefixed the contacts’ names to add a personalized touch. The app, most often, is an online sex simulator game. But in the background, it initiates contact with a command-and-control (C&C) server to access a hard-coded list of addresses, and to encrypt and decrypt the files. Upon sending the messages, Filecoder then scans the infected device to encrypt most file types — including text files and images — with the extension “.seven.” This effectively prevents victims from accessing files stored in the device. But archived files (.zip and .rar) larger than 50MB and Android extensions such as .apk and .dex appear to be exempted. ESET observed that the encryption file list has been copied from the notorious WannaCry ransomware attack that targeted Windows PCs by encrypting data and demanding ransom payments in Bitcoins. While Filecoder doesn’t lock you out the device, it makes use of the RSA algorithm to encrypt the device’s contents. A private and public key pair is generated, and the private key, in turn, is encrypted using a hard-coded public key and sent to the C&C server. If the ransom is paid, the attacker offers to decrypt the private key, and send that private key back to the victim to decrypt the files. “Any encrypted files can be recovered without help from the attackers,” ESET researchers wrote. “However, if the developers fix the flaws and the distribution becomes more advanced, this new ransomware could become a serious threat. Interestingly, the ransom note warns that data will be lost after 72 hours, but ESET found no evidence in the software code to support this claim. Unlike other kinds of ransomware, the requested Bitcoin ransom amount is partly dynamic: the first few digits are fixed (0.01) and the remaining six digits vary based on the user ID generated by the malware. The researchers have not disclosed how many devices have been affected by Filecoder. But inspecting the bit.ly links, they found it had been clicked 59 times, with most clicks coming from mainland China, the US, and Hong Kong. While Android continues to face a wave of security threats — Agent Smith, Monokle, and other forms of malware — it’s always advisable to stick to Google Play (or other reputable app stores) for downloading apps, keep your phone’s software up to date, and be cautious of the permissions requested by apps.